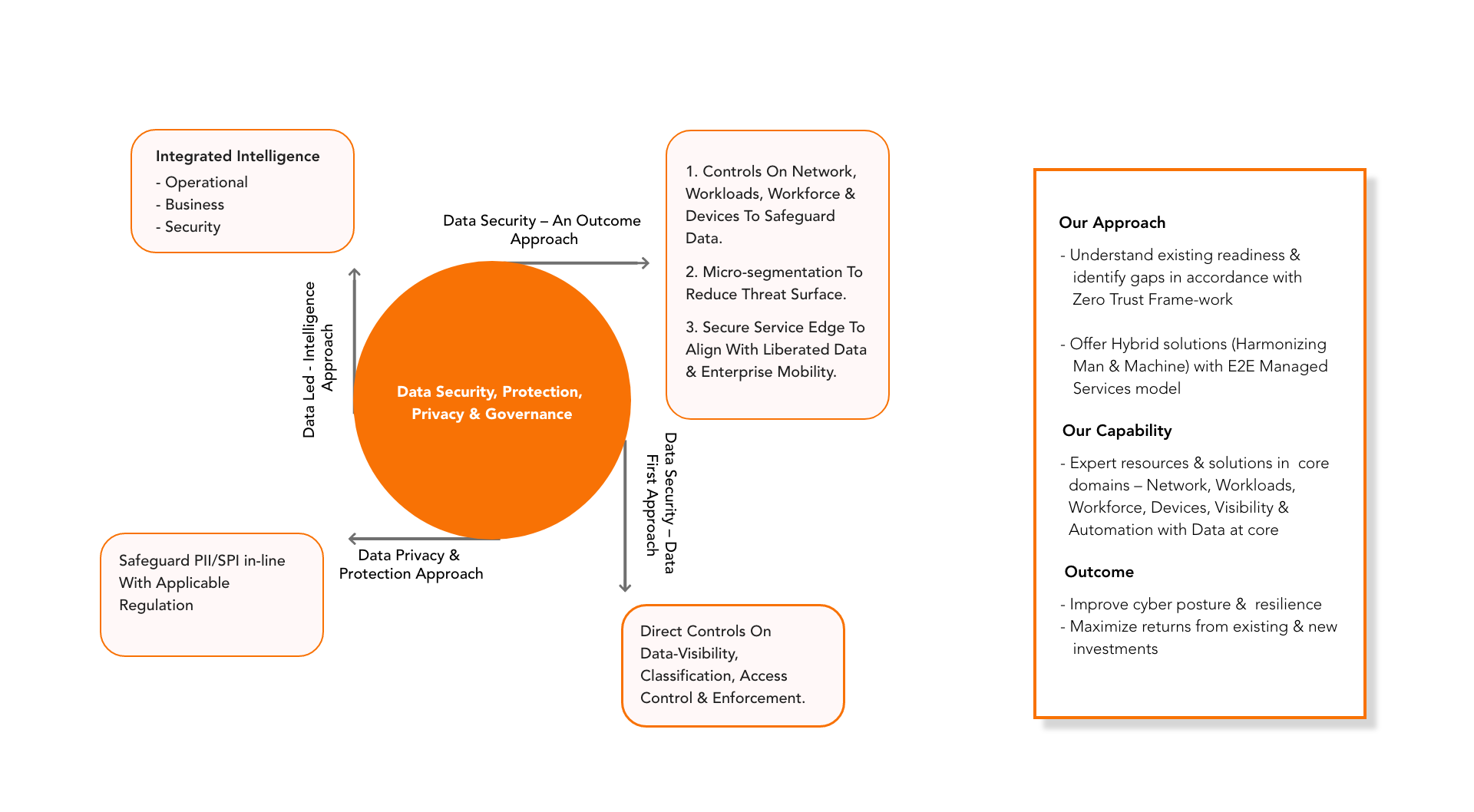
Joined-Up Approach To Fortify Enterprise Data
With the rise in digital led businesses and the increasing interconnectedness of systems, organizations now generate and collect vast amount of data. This data holds valuable insights and information that can be leveraged to improve customer experience, guide innovation, architect compelling products, improve operations, and gain competitive advantage.