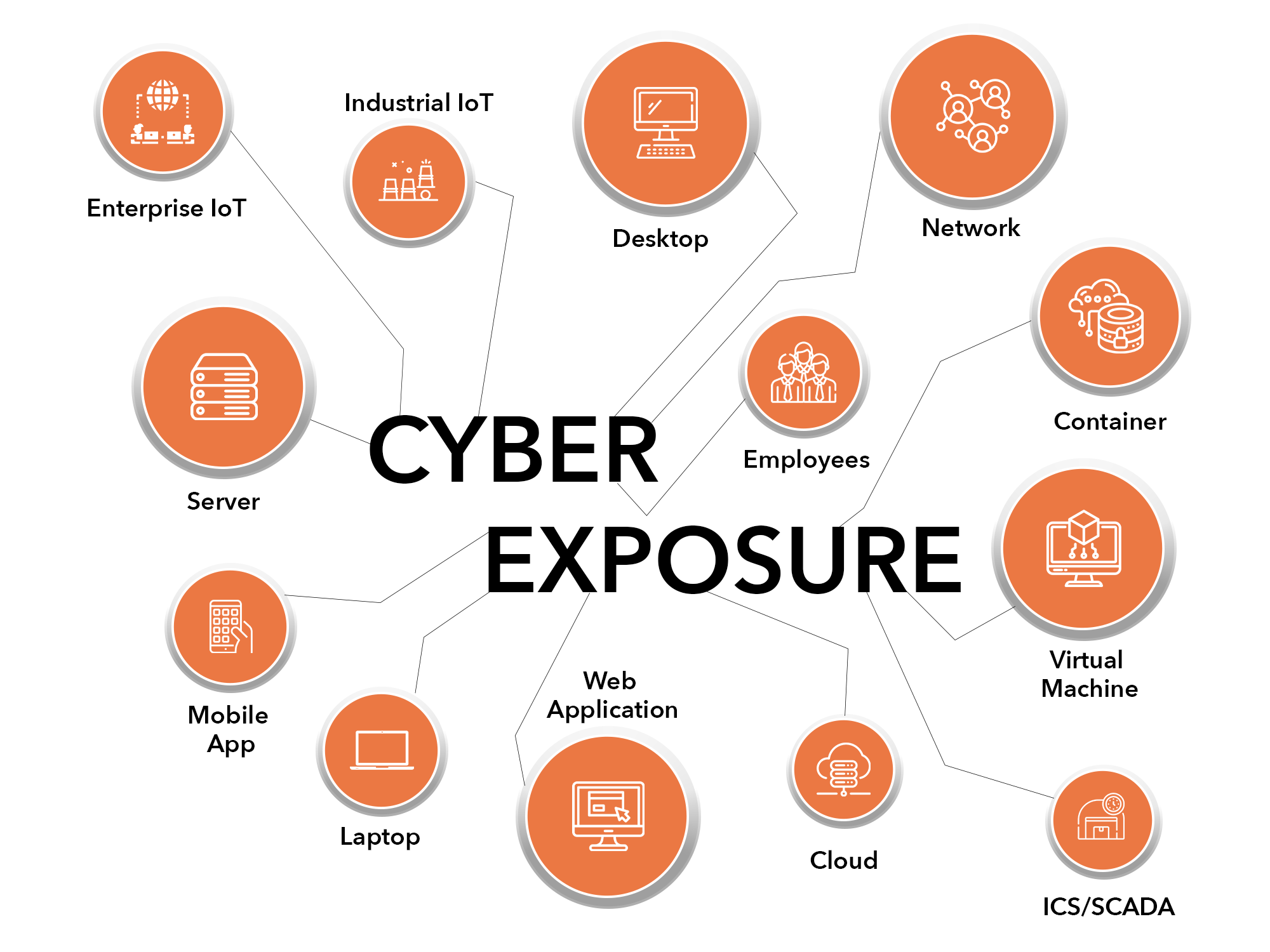
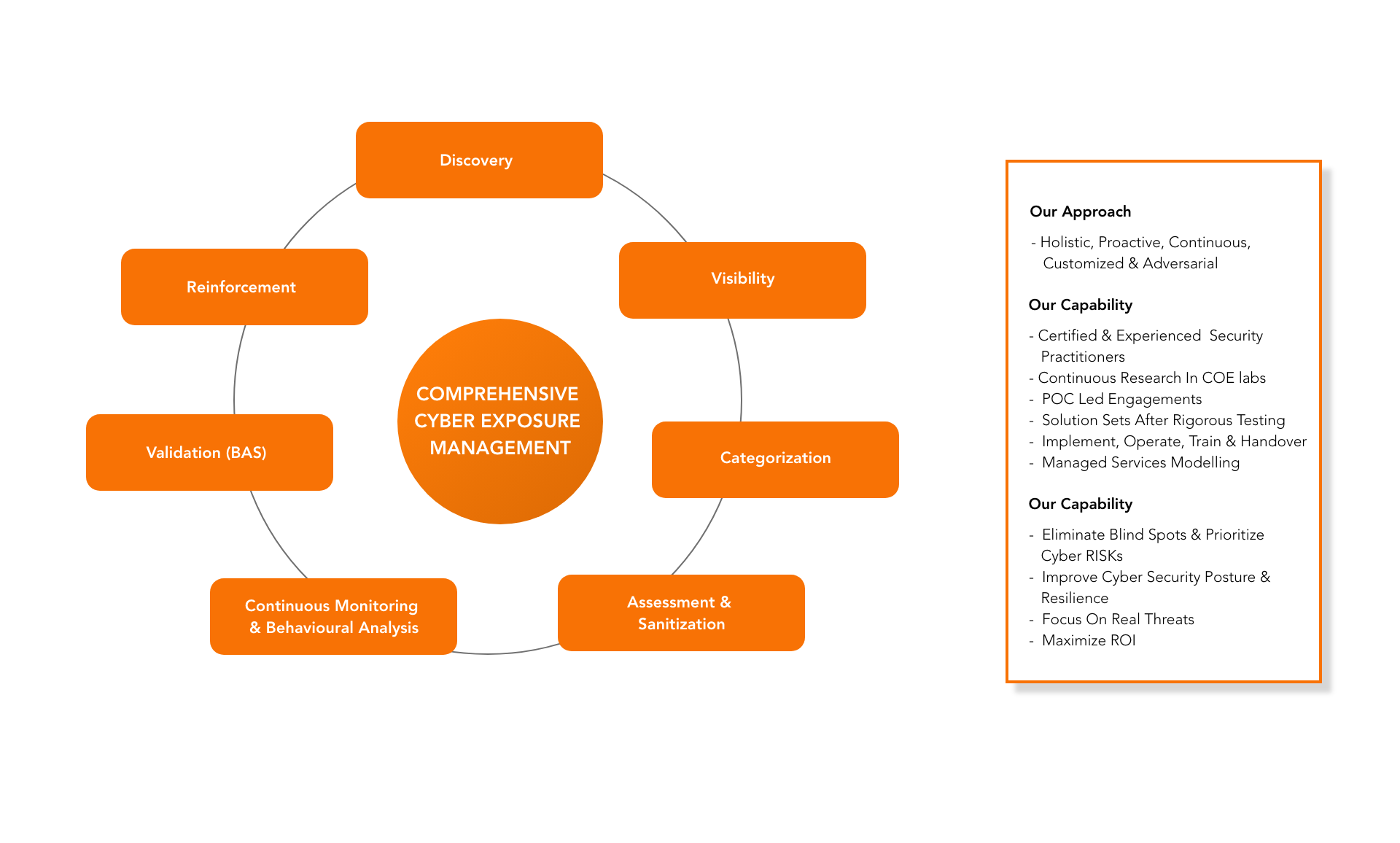
About Cyber Exposure Management
The origin of “Cyber Exposure Management” can be traced back to the nascent stages of cybersecurity, which was predominantly based on reactive, patch-based approach. Vulnerability assessments emerged as a precursor to contemporary cyber exposure management, aimed at identifying weaknesses in Network, Cloud, Applications, Data & People to name a few.
However, throughout the evolution of cyber exposure management, the cybersecurity landscape has been marked by a perpetual cat-and-mouse game with hackers. Just as vulnerabilities were identified and addressed, hackers developed new methods to breach defences.